In Part 1 of this series, we asked if we fully understand the threat to our autonomy and well-being that arises when we use the internet. Now we are going to look at more closely at how Big Tech gets hold of our data without us being being aware or informed.
Previously, we highlighted one of the original visions for identity on the internet: "in cyberspace you can be whoever you want to be". We could assume multiple identities on-line and manage them ourselves, often privately.
Over the past ten years or so, a more sinister vision has developed, this time led by the Tech corporations ("Big Tech"). This vision can be summed up as "We know who you are, we know where you live, how you live, how you want to live and how you will live in the future.
Invasion of privacy has gone beyond stealing card details or some of your files. These risks are insignificant compared to the harm that can be done when your identity itself is stolen. Consider what could happen if your passwords and account details are stolen. The temptation for "bad actors" is clear: the technology is already available to spy on us, to misdirect us and, in the end, to control us.
Up to now, our data has been sold to other corporations and the emphasis has been on influencing and controlling our shopping habits. But in recent years, we are seeing a merger of State and corporate power as governments are seduced into these practices by the promise of 'a power over the people without vulnerability to rebellious acts'. Tech companies are playing a more active role in censorship, pushing people towards the official "narrative", labelling research that challenges the narrative as "misinformation", allowing "character assassination" and, in the end, banning people from their platforms. The leading culprits here are the fashioners of the so called 'Web 2.0': Facebook, Google (with YouTube) and Twitter.
There is a progression happening here:
- identity tracking leading to
- identity theft leading to
- identity faking where false information is created with false attributions to you.
But for this to work, Big Tech needs our personal information. The easiest place for them to start is with our social media accounts. Keep this in mind.
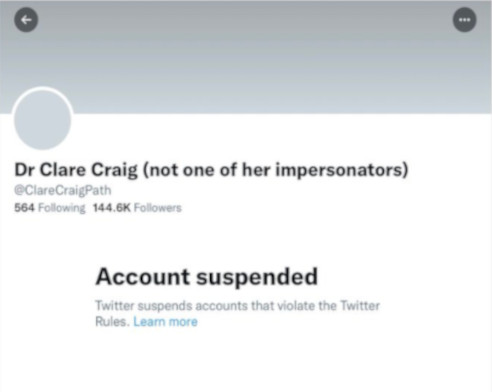 |
| Dr Clare Craig BM BCh FRCPath is a medical doctor and is a specialist Diagnostic Pathologist. She has been investigating the results of drug trials carried out by pharmaceutical corporations. When she shared her research results on Twitter she was banned from the platform. Following a vociferous campaign by high-profile Twitter users, she was re-instated. |
 |
Two Factor Authentication - how Big Tech spies on us.
Many of you will now be used to a two-component process of logging in to websites. In the trade, this is known as "Two Factor Authentication" (2FA). After you submit your initial login, the site sends a message to your mobile phone with a special code that you enter to complete your login - an "external verification".
The highest level of security, in regards to personal accounts and online identification, would be provided by three factors:
- something you know (e.g. password, personally known info e.g. first pet's name, used as security questions)
- something you are (retina scan, voice match, fingerprint, DNA)
- something you hold or own (phone, key card / card reader, dongle (USB key), code device (secure key).
This means there are plenty of options for choosing two out of those three factors. For example, within the FOSS / Open Rights / Privacy Rights IT community, cryptographic keys on secure USBs are used quite often. That is from the third group of factors but inherently private and easier to keep secure. Governments and Big Tech clearly haven't used security reasons when they pushed for 2FA via mobile phones. The mobile network is very insecure; phone numbers are widely shared leading to them being hijacked by criminals and open to spoofing; and there is a massive over-reliance on one device - again destroying it's security viability. It's one of these questions, where bad advice, ignorance or incompetence can't explain the bad choice. And there's been no lack of challenge to this choice - we do have to consider either selfish, corrupt or even malicious motives.
The initial reasons for introducing 2FA may have been benign. But it becomes clear that corporations like Facebook and Google have subverted this process so that they can spy on us. These corporations introduced 2FA under the guise of "protecting your social media account". (Does my social media account need this level of protection? It's not as if it's my bank account or something similar) We suspect that their real purpose was to get your phone number which could then lead to your real-world identity. That real-world identity will then be tied to your social media account. If people know your phone number then they can find out who you are.
The key piece of the data-harvesting challenge is your real-world identity. Without that, the disparate pieces of data that you give out as you move around the internet have no "value" - they can't be linked together and in particular to you. By sifting through the "dross" of data, and allocating it to a real person, tech corporations can transmute it into "nuggets of gold".
There is a promotional video from Rob Braxman that explains this threat in more detail.
| Rob Braxton gives some tips on how to resist |
 |
There are ways of carrying out 2FA without compromising user's privaxcy. But Google is showing determination to identify all the devices that you use and tie them to your identity. This is known as "cross device tracking" - they want all your devices linked to your mobile phone.
Your phone is your ID
This is only the beginning, what about the operating systems that power your smartphone, such as Android (Google) and IoS (Apple)? What about numerous apps that people install on their smart phones? What are they monitoring and where does your personal information go?
It is becoming clear that your smartphone is an identity card combined with an electronic tag. It knows what people do in your current location. It knows if you've not done that yet. It then knows what you are most likely to do next. If you do something different - it will update its prediction model.
Anti-social media
The best way to find out what you are thinking is to examine your social media accounts. Many social media platforms appear to be designed to find out your:
- political views
- religious beliefs
- social circle
- and your level of gullibility.
This will allow them to manipulate what you see and even censor your content. It could also allow Authorities to "nudge" (to influence) your actions even before the "sticks and carrots" of a social credit system are overlaid on the society of smartphone users.
Welcome to the Panopticon
| The Panopticon is a design for a prison drawn up by Jeremy Bentham the 18thC political philosopher. In this design, all prisoners could be watched at all times, without them knowing whether they were observed, or not. |
 |
Do we really want to end up in a Panopticon? Our advice remains the same: be very careful what you post on-line. Self-discipline is needed. And we must resist attempts to invade our privacy. As Rob Braxman points out, significant resistence signals a "business risk" to the Corporations, and this tends to alter their behaviour.
We will return to this in a future article.
Northern Edge cookie policyNorthern Edge does not store cookies. As a result, we have no idea who is reading this, nor any other of our articles. You are reading Northern Edge without providing us with any information whatsoever. We are sure that you will write to us with comments and feedback when you feel motivated to do so. And we are happy to discuss the publication when we see you at one of our face-to-face meetings. |